copyright can be a easy and reliable platform for copyright buying and selling. The application capabilities an intuitive interface, high order execution pace, and valuable current market Assessment tools. It also offers leveraged buying and selling and a variety of buy styles.
copyright exchanges vary broadly in the products and services they provide. Some platforms only supply the ability to invest in and offer, while others, like copyright.US, provide Highly developed expert services Together with the basics, including:
Further stability measures from possibly Safe Wallet or copyright might have reduced the probability of the incident occurring. As an illustration, utilizing pre-signing simulations would've allowed staff to preview the desired destination of a transaction. Enacting delays for big withdrawals also would've offered copyright time and energy to evaluate the transaction and freeze the funds.
Several argue that regulation powerful for securing financial institutions is considerably less powerful while in the copyright Place due to marketplace?�s decentralized character. copyright demands far more protection rules, but In addition, it wants new options that consider its variations from fiat financial check here establishments.
Also, it appears that the menace actors are leveraging revenue laundering-as-a-support, furnished by organized crime syndicates in China and nations around the world all through Southeast Asia. Use of the company seeks to additional obfuscate cash, reducing traceability and seemingly using a ?�flood the zone??tactic.
This tactic seeks to overwhelm compliance analysts, regulation enforcement, and blockchain analysts by executing A large number of transactions, both of those by way of DEXs and wallet-to-wallet transfers. After the high-priced attempts to cover the transaction path, the ultimate target of this process are going to be to transform the funds into fiat forex, or currency issued by a govt just like the US greenback or even the euro.
These threat actors ended up then in a position to steal AWS session tokens, the momentary keys that allow you to ask for non permanent credentials on your employer?�s AWS account. By hijacking active tokens, the attackers have been ready to bypass MFA controls and obtain usage of Secure Wallet ?�s AWS account. By timing their initiatives to coincide While using the developer?�s typical get the job done hours, Additionally they remained undetected until eventually the actual heist.}
 Yasmine Bleeth Then & Now!
Yasmine Bleeth Then & Now! Elin Nordegren Then & Now!
Elin Nordegren Then & Now! Mason Reese Then & Now!
Mason Reese Then & Now!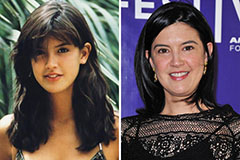 Phoebe Cates Then & Now!
Phoebe Cates Then & Now! Mary Beth McDonough Then & Now!
Mary Beth McDonough Then & Now!